In today’s dynamic digital sphere, safeguarding your online presence has never been more critical. With evolving cyber threats, the need for the best VPN in 2024 is essential. A Virtual Private Network (VPN) stands as your digital shield, encrypting data, concealing your identity, and facilitating secure access to restricted content.
What is the most trusted VPN in the world? Our comprehensive testing reveals ExpressVPN as the top choice, maintaining BESTVPN’s top spot for its unwavering commitment to privacy and remarkable speeds. Surfshark follows closely as another standout contender among our top picks.
From shielding personal data to unlocking global content, VPNs offer versatile solutions. Our analysis presents the year’s top VPNs, guiding you toward tailored choices that align with your specific requirements.
In this guide, we explore the best VPN services of 2024, assessing their speed, security, features, and pricing to empower your informed selection and safe usage.
Quick Summary: Best VPN Testing Statistics
| Number of VPNs Tested | 31 |
|---|---|
| Duration for which each VPN was tested | 6 months |
| Highest Monthly cost | $12.95 |
| Available contract lengths | 1 month, 6 months, 1 year, 2 years |
Best VPN Services Of 2024 at a Glance
When it comes to choosing a VPN, there are a few factors you need to take into account. These are one of the top-tier VPN providers with robust security protocols, a zero logs policy, fast servers, and reliable 24/7 customer support.
- ExpressVPN – The Best VPN Service: With 3000 servers in 105 countries, it is one of the best VPN providers. It offers fast speeds with prices starting from just US$ 6.67 /mo - Save up to 49% with exclusive 1-year plans + 3 months free.
- Surfshark – The Best Affordable VPN: With 3200 servers in 100 countries, it is the best affordable VPN for streaming and unblocking geo-restricted content. Prices start from US$ 2.49 /mo - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee with a 30-day money-back policy.
- NordVPN – Best VPN for Security: It is the best VPN for security, streaming, and unblocking geo-restricted content with 6000 servers in 61 countries. Enjoy ultra-fast server connection speeds and connect up to 6 devices simultaneously. Prices start from US$ 3.99 /mo - Save up to 63% with exclusive 2-year plan + 3 months free for a friend with a 30-day money-back policy.
- CyberGhost – Best VPN Service for Unblocking geo-restricted content: It is the best VPN for unblocking geo-restricted content with 7900 servers in 100 countries. Get ultra-fast server connection speeds and connect up to 7 devices simultaneously. Prices start from US$ 2.03 /mo - Save up to 84% with exclusive 2-year plans + 4 months free with a 30-day money-back policy.
- Private Internet Access – Best VPN Choice for Beginners: It is the best VPN for beginners, with 35,000+ servers in 91 countries for torrenting and unblocking geo-restricted content. Enjoy ultra-fast server connection speeds and connect unlimited devices simultaneously for $3.99/mo with a 30-day money-back policy.
- IPVanish – Best VPN for Beginners: It provides an easy-to-use interface with 2200+ servers in 75+ locations. Enjoy ultra-fast server connections, connect unlimited devices, and get it for $2.92/mo with a 30-day money-back policy.
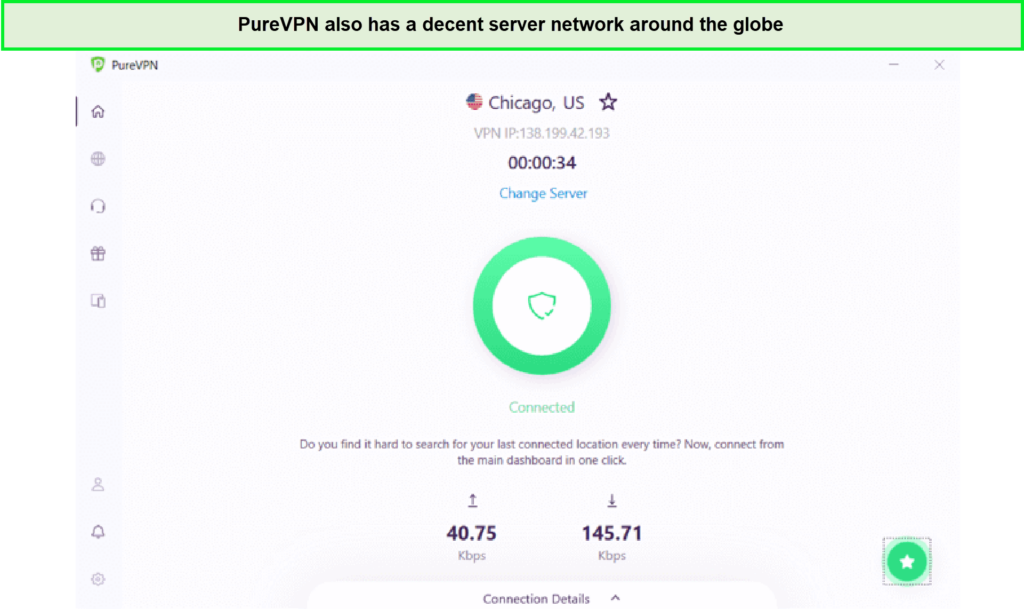
- PureVPN – Best VPN with feature-rich interface: It offers a feature-rich interface with 6500 servers in 78. Connect up to 10 devices simultaneously, and get it for US$ 3.29 /mo and a 31-day refund.
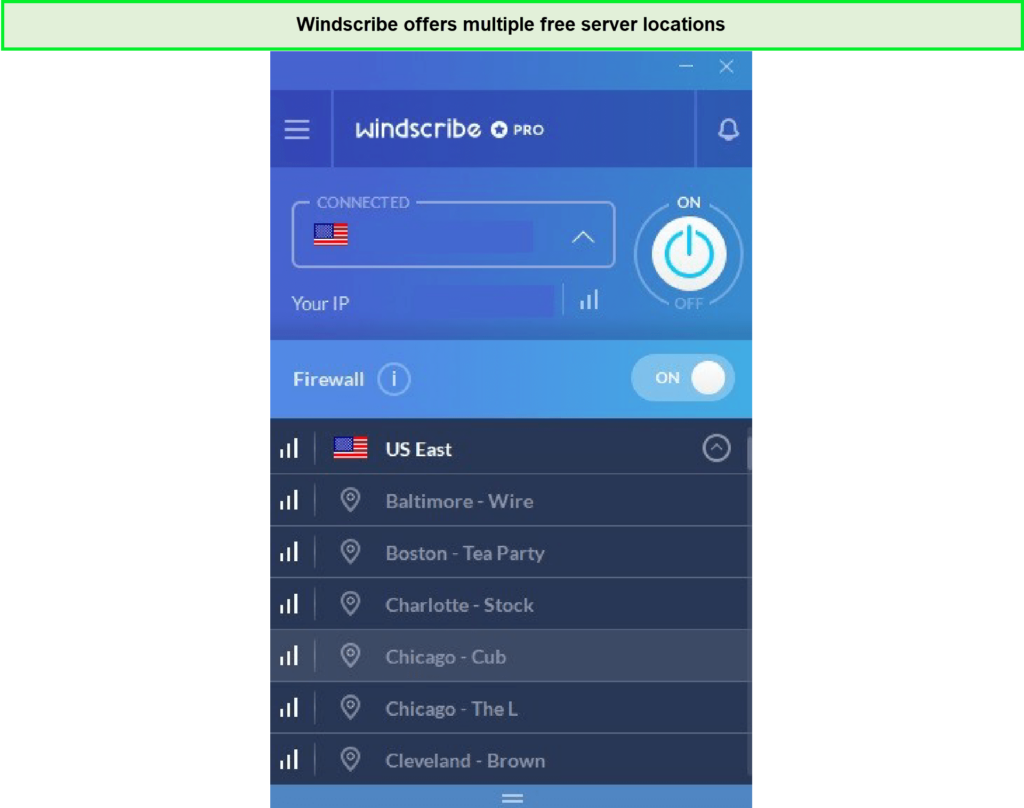
- Windscribe – Best Free VPN: It offers a free VPN plan with servers in 63 countries and 110 cities. Enjoy fast-speed servers, connect unlimited devices, and get it for $5.75/mo with a 3-day money-back policy.
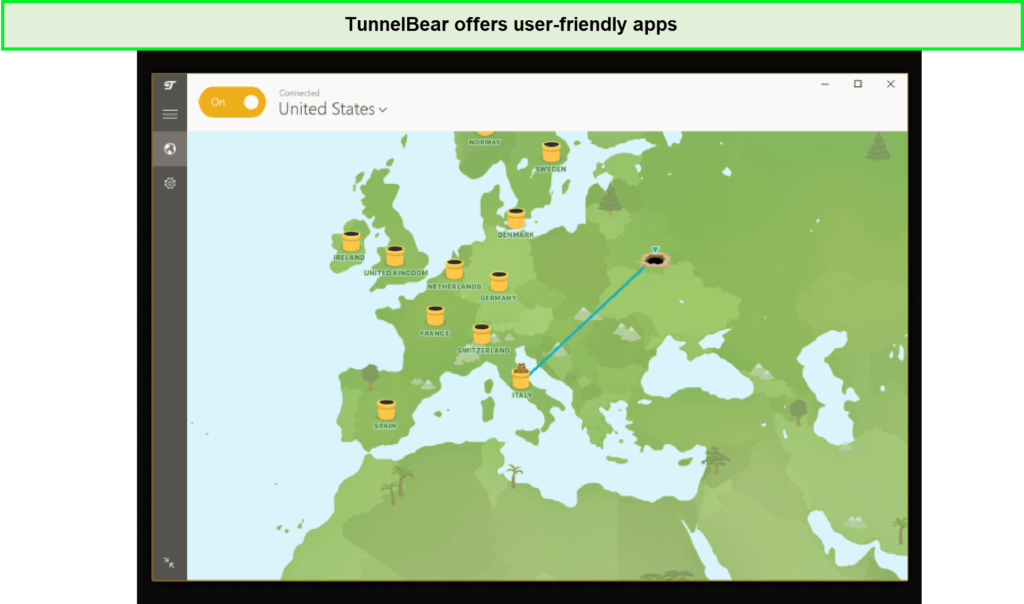
- TunnelBear – Best UI VPN: It provides user-friendly and interactive apps with over 5000 servers in 47+ countries. Enjoy fast-speed servers, connect unlimited devices, and get it for $3.33/mo on a 67% discount with no clear refund policy.
- VyprVPN – Privacy-friendly VPN: It is privacy-friendly and safe with 700+ servers in 90+ locations. Enjoy high-speed servers, connect up to 10 devices simultaneously, and get it for $5/mo with a 30-day refund.
Update, 8th November, 3:01 AM: Updated the article with the information regarding PIA’s expansion of servers from 84 to 91 countries.
For more detailed VPN reviews, proceed to the next section or check our FAQs.
Quick Comparison – Best VPN Services of 2024
Here’s a side-by-side comparison of the top VPN services in 2024:
| VPN | Ranking | Servers | Speed | Price | Logging Policy | Money Back Guarantee | Unblocking | Live Customer Support | Compatibility | Visit Sit |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 3000 | 90.29 Mbps | US$ 6.67 /mo - Save up to 49% with exclusive 1-year plans + 3 months free | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | ExpressVPN website | |
 |
2 | 3200 | 89.99 Mbps | US$ 2.49 /mo - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | Surfshark website |
 |
3 | 6000 | 82.22 Mbps | US$ 3.99 /mo - Save up to 63% with exclusive 2-year plan + 3 months free for a friend | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | NordVPN website |
 |
4 | 7900 | 82.22 Mbps | US$ 2.03 /mo - Save up to 84% with exclusive 2-year plans + 4 months free | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | CyberGhost website |
 |
5 | 35,000+ | 75.46 Mbps | $3.99/mo | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | Private Internet Access website |
 |
6 | 2,200+ | 72.13 Mbps | $2.92/mo | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | IPVanish website |
 |
7 | 6,500+ | 81.45 Mbps | $2.05 | Strictly no-logs | 31-day refund | Netflix, Hulu, BBC IPlayer, regional services | 24/7 | Windows, Android, iOS, and others | PureVPN website |
 |
8 | 500+ | 66.17 Mbps | $5.75/mo | Strictly no-logs | 3-day | Netflix, Hulu, BBC IPlayer, regional services | Not Available | Windows, Android, iOS, and others | Windscribe website |
 |
9 | 5,000+ | 65.19 Mbps | $3.33/mo | Strictly no-logs | None | Netflix, Hulu, BBC IPlayer, regional services | Not Available | Windows, Android, iOS, and others | TunnelBear website |
 |
10 | 700+ | 18.95 Mbps | $5/mo | Strictly no-logs | 30-day | Netflix, Hulu, BBC IPlayer, regional services | Not Available | Windows, Android, iOS, and others | VyprVPN website |
Best VPN Services of 2024 [ In-Depth Analysis]
Are you looking to buy a VPN service? Let us make the decision-making process a bit easier. Below is a list of the best VPNs for 2024, each offering an impressive list of benefits.
The process of reviewing the below providers took us over two weeks, and as you can see is different from what you will see on most websites. Why? Because we actually TEST each provider!
1. ExpressVPN – The Best VPN Service

Key Features
- Best VPN service for streaming and unblocking geo-restricted content
- 3000 in 105 countries
- Ultra-fast server connection speeds
- 5 device connections simultaneously
- Pricing starts from US$ 6.67 /mo - Save up to 49% with exclusive 1-year plans + 3 months free with a 30-day money-back policy
- 24/7 live chat support
ExpressVPN stands out as the best VPN service provider on the market, renowned for its exceptional encryption capabilities. Utilizing the industry-standard 256-bit AES encryption, ExpressVPN takes data security to the next level. But their dedication to safeguarding user privacy doesn’t stop there; they offer a range of secure VPN protocols to further fortify their network. Notably, ExpressVPN has developed its own protocol, Lightway, which excels in both encryption strength and efficiency.
While ExpressVPN may come with a slightly higher price tag compared to some competitors, its unmatched commitment to security justifies the cost. For users who prioritize the utmost protection, ExpressVPN is a worthwhile investment. Rest assured that your data remains shielded and secure, regardless of your location or online activities. With ExpressVPN, you can confidently browse the internet with peace of mind.
| Does ExpressVPN have the following features? | |
|---|---|
| Lightway Protocol | Yes |
| Strict no-log policy | Yes |
| Kill switch | Yes |
| Split-tunneling | Yes |
| Can unblock Netflix? | Yes |
| Torrenting | Yes |
Why we selected ExpressVPN
We selected ExpressVPN, which is headquartered in the secure jurisdiction of the British Virgin Islands, because of an exceptional all-around VPN service that truly impressed us during our testing. We found it to be remarkably fast, making it an excellent choice for users who prioritize speed alongside privacy.
One aspect that stood out to us was ExpressVPN’s extensive server network. With over 3000 servers spread across 105 countries, it offers an impressive global presence. This wide coverage allowed us to easily bypass geo-restrictions and access content from various regions. We were particularly pleased with its ability to effortlessly unblock Netflix with ExpressVPN and other libraries, ensuring a seamless streaming experience.
Speed is a crucial factor for any VPN user, and ExpressVPN delivered a commendable performance in this regard. During our tests, we found it to be one of the fastest VPNs, consistently experiencing average download speeds of 90.29 Mbps and upload speeds of 76.92 Mbps. This impressive speed allowed us to browse, stream, and download content without any noticeable lag or buffering.
ExpressVPN’s split tunneling feature added another layer of versatility to its offering. We appreciated the ability to selectively route specific traffic through the VPN while allowing other applications or devices to bypass it. This level of control enhanced our overall browsing experience.
In terms of device compatibility, ExpressVPN offers native apps for all major operating systems and devices. We installed ExpressVPN on Android and iPhone to check its usability and were satisfied with the results. We also checked for its compatibility with streaming devices and found ExpressVPN working with Kodi, Firestick, Smart TVs, and other devices. We were also delighted to find that it provides a reliable app for DD-WRT and Tomato routers, allowing users to install ExpressVPN on routers, directly for comprehensive protection throughout their network.
Ignite your passion for sports with ExpressVPN, a gateway to unparalleled streaming experiences. As you immerse yourself in the world of Premier Sports, rely on ExpressVPN, your key to an enhanced sports viewing journey and the Best VPN for Premier Sports in USA. Say goodbye to geo-restrictions and hello to seamless access with the best VPN for Virgin TV in USA.
A notable highlight is ExpressVPN’s commitment to user privacy. Their verified no-logs policy, which even withstood scrutiny from Turkish authorities, is audited by reputable firms such as PWC and Cure53. This level of transparency and external validation provided us with confidence in their privacy claims.
Additionally, ExpressVPN took a significant step towards enhancing security and privacy by shifting all their servers to RAM-disk mode. This update ensures that no logs are stored physically on the servers, further bolstering user privacy and improving overall server speeds.
While ExpressVPN impressed us on multiple fronts, it’s important to note that it comes at a higher price point compared to some other VPN services. However, considering the exceptional performance, strong privacy measures, and extensive features it offers, we believe the cost is justified for users seeking top-tier VPN service.
If you want a blazing-fast VPN while streaming channels like Netflix, Disney+, and Hulu, ExpressVPN is the right choice. You can also torrent with ExpressVPN, and play various geo-restricted games with low ping rates. In fact, it’s a good gaming VPN and best VPN for DDoS protection that is compatible with various game consoles, including PS4, Xbox, and more. It is also one of the best crypto-trading VPNs that allow you to carry out secure transactions from wherever you are. While its cost may seem high, it’s worth it!
ExpressVPN offers top-notch torrenting features, making it the best VPN for uTorrent users. With its robust encryption and strict no-logs policy, ExpressVPN ensures your online activities remain private and secure while torrenting. The high-speed servers and unlimited bandwidth further enhance the user experience, making ExpressVPN an ideal choice for those seeking the best VPN for uTorrent downloads in USA.
ExpressVPN Lightway Protocol
ExpressVPN’s development of the proprietary Lightway protocol demonstrates its commitment to advancing VPN technology. We were thoroughly impressed by this innovative addition to their service. Unlike other protocols like OpenVPN, Lightway boasts a streamlined design with just 2,000 lines of code.
We had a consistent connection through ExpressVPN’s Lightway Protocol.
This simplicity contributes to its lightweight nature and ensures a seamless user experience, all while maintaining top-notch security. ExpressVPN’s Lightway protocol truly sets them apart as a leader in the VPN industry. It helps achieve considerably fast results during our ExpressVPN speed test.
Here is how Lightway stacks up against OpenVPN:
| Features | Lightway | OpenVPN |
|---|---|---|
| Battery consumption | Low | Mid to high |
| Year established | 2001 | 2020 |
| Security | Secure | Secure |
| Speed | Faster | Fast |
Top-Notch Security and Privacy Protection
ExpressVPN’s Lightway protocol, apps, and browser extensions have undergone rigorous security audits, leaving no room for doubt about their impenetrability. These audits reassure us that our sensitive information remains securely shielded from prying eyes. Furthermore, the esteemed auditing firm KPMG confirmed ExpressVPN’s unwavering commitment to its no-logs policy in 2024, cementing our trust in their privacy practices.
Additional security and privacy features that helped cement its position as the number one VPN in our minds include:
- Privacy Protection: ExpressVPN operates from the British Virgin Islands, situated outside the oppressive grasp of the 14-Eyes Alliance. By leveraging TrustedServer technology with RAM-based servers, ExpressVPN ensures that our data is wiped clean after every reboot, leaving no traces behind. This exceptional level of privacy protection ensures our digital footprint remains untraceable.
- Military-Grade Encryption: ExpressVPN’s encryption standards are a force to be reckoned with. Combining AES 256-bit encryption, SHA512 hashing, and a 4096-bit RSA key, it erects an impenetrable fortress that even the most skillful hackers struggle to breach. Adding to our peace of mind is the perfect forward secrecy feature, guaranteeing that even if an encryption key were to be compromised, our past and future communications would remain safeguarded.
- Fortified Defense against Data Leaks: ExpressVPN’s Network Lock acts as an impenetrable shield, ensuring our data remains confidential even if our connection to the VPN server is unexpectedly interrupted. This kill switch functionality shields us from potential exposure. Moreover, ExpressVPN takes no chances with DNS/IP and WebRTC leak protection, assuring us that our online activities remain concealed from prying eyes.
- Diverse Protocols for Enhanced Flexibility: ExpressVPN goes beyond expectations by offering a wide array of protocols, including Lightway, OpenVPN, IKEv2, and L2TP/IPsec. This abundance of choices empowers us to tailor our VPN connection to suit our specific needs, striking the perfect balance between security and flexibility.
- Unmasking Threats with the Threat Manager: ExpressVPN takes proactive measures to shield us from malicious entities lurking in the digital realm. Their Threat Manager feature equips us with a comprehensive blocklist, effectively identifying sites notorious for tracking and malware. This robust defense system ensures our devices never communicate with these dubious servers, bolstering our security posture.
- Obliterating Censorship Barriers: ExpressVPN’s remarkable obfuscation prowess serves as a potent weapon in the face of strict censorship regimes. Not only does it enable access to restricted content, but it even triumphs over the notorious Great Firewall of China. This remarkable feature allows us to exercise our digital freedom without limitations, no matter where we are.
Dependable Customer Support and Reliable Guarantee
As a bunch of discerning reviewers ourselves, we can understand the importance of providing an opinionated perspective. Trying out ExpressVPN comes with the added benefit of a risk-free experience, thanks to its generous 30-day money-back guarantee. During our testing, we found the refund process to be straightforward and hassle-free.
Utilizing their convenient 24/7 live chat support, we requested to cancel our ExpressVPN subscription for a refund and were pleasantly surprised by the seamless assistance provided. The friendliness of the agent added to the experience. The agent asked a few questions about our time using the company’s product and promptly approved the refund. It was a relief to see the funds back in our account just a few days later. Another point that made the case easier for us is that you can even test the service out for free through a risk-free 30-day ExpressVPN free trial.
ExpressVPN’s commitment to 24/7 support is commendable, ensuring that users have assistance whenever they need it. Whether you have inquiries, or technical issues, or require guidance, their round-the-clock support team is readily available to provide prompt and helpful responses. As per our experience, we found it to be the VPN provider with the best customer support.
Considering the cost, it’s important to note that ExpressVPN falls on the higher end of the pricing spectrum. While it may be a bit more expensive compared to some competitors, the level of service, advanced features, and robust security measures justify the investment for those seeking a top-tier VPN experience.
Additionally, ExpressVPN offers a free trial that allows users to test the service risk-free. This enables prospective customers to experience the VPN firsthand, ensuring it meets their specific needs before committing to a subscription.
To receive more insights into the best VPN 2024, read this detailed ExpressVPN review!
- Strong privacy features for maximum protection.
- Versatile apps across multiple platforms.
- Great for secure and fast torrenting.
- Outstanding round-the-clock customer support.
- Blazing-fast speed rates for all sorts of online activities.
- More expensive than other providers
2. Surfshark – The Best Affordable VPN
Key Features
- Best affordable VPN service for streaming and unblocking geo-restricted content
- 3200 servers in 100 countries
- Ultra-fast server connection speeds
- Unlimited device connections simultaneously
- Price: US$ 2.49 /mo - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee with a 30-day money-back policy
- 24/7 live chat support
Surfshark is the best affordable VPN for streaming due in no small part, to the low prices of its long-term plans that have cemented its status as one of the cheapest VPNs available. We have been thoroughly testing out Surfshark, and we are very impressed with what we have found. The VPN takes security seriously and offers the usual privacy features of VPNs, but often with added twists that make them extra secure. For example, Camouflage Mode allows you to use a VPN without your network administrator, school, or government knowing that you’re using one.
We are impressed with Surfshark’s commitment to security. The VPN uses strong encryption and has a strict no-logs policy. It also offers a variety of other security features, such as DNS leak protection and a kill switch.
In addition to being a VPN, Surfshark also offers a variety of other cybersecurity features. These features are included in the Surfshark One subscription, which also includes antivirus software, data leak detection, and a secure search engine.
| Does Surfshark have the following features? | |
|---|---|
| Whitelister | Yes |
| Camouflage mode | Yes |
| Kill switch | Yes |
| Split-tunneling | Yes |
| Can unblock Netflix? | Yes |
| Torrenting | Yes |
Why we selected Surfshark
We selected Surfshark for the following reasons:
Servers and Countries: Surfshark’s expansion since its launch in 2018 is truly remarkable. With over 3200 servers spread across more than 100 countries, it ensures a wide range of connection options for users.
The sheer number of servers provides ample opportunities for secure and reliable connections. However, we noticed that performance varied across different locations, with some servers outshining others in terms of speed and reliability.
| Country | Surfshark Locations |
|---|---|
| France | 3 |
| United Kingdom | 8 |
| United States | 33 |
| Canada | 2 |
| Australia | 5 |
Speed: Surfshark impresses with its consistent speed capabilities. Delivering an average download speed of 89.99 Mbps and an upload speed of 86.25 Mbps, it enables seamless browsing, streaming, and downloading experiences. While external factors can impact speed, Surfshark speed performs admirably under normal conditions.
Split Tunneling: One feature that sets Surfshark apart is its convenient split tunneling functionality. This allows users to selectively choose which apps or websites bypass the VPN connection, optimizing bandwidth and ensuring fast connections for specific tasks. It’s a handy feature that caters to individual preferences and enhances overall flexibility.
Stealth Mode: While Surfshark claims to offer a stealth mode for evading strict censorship measures, we found it to be somewhat inconsistent in practice. While it does provide some level of obfuscation, it may not consistently bypass rigorous restrictions. That’s also the reason why we could easily access Hulu with Surfshark without any proxy errors. However, it should be noted that this feature is still beneficial for accessing restricted content in many cases.
Devices and Streaming: Surfshark excels in providing a user-friendly experience across various devices. Its intuitive interface makes it the best VPN for PC and mobile users. We could easily set up Surfshark on Smart TV, Kodi, Firestick and other streaming devices. Navigating through the app and controlling its features is a breeze and using Surfshark on Firestick in USA allows you to stream your favorite content without any hassle, making the experience effortless and enjoyable.
Also, Surfshark is ideal for iPhone enthusiasts, Surfshark boasts an effortless VPN integration. Elevate your mobile security with Surfshark on iPhone in USA, experiencing smart controls and seamless browsing. Explore the convenience of Surfshark with iPhone and other operating devices, combining simplicity and top-notch performance.
Moreover, Surfshark has gained a reputation as the go-to VPN for streaming. It effortlessly unblocks popular platforms such as Voot, and Hotstar from anywhere. Due to its remarkable unblocking abilities, it is named the best VPN for Netflix, unblocking multiple libraries on Netflix with Surfshark from all over the globe. Its ability to access region-locked content is a major advantage for entertainment enthusiasts and we consider it to be one fine Disney Plus VPN.
Torrenting and Ram Only Servers: Surfshark embraces the needs of torrenting enthusiasts by allowing P2P file sharing on its network. This feature, combined with its extensive server network, ensures optimized speeds and secure connections for torrenting activities. Additionally, Surfshark’s utilization of RAM-only servers, referred to as TrustedServer technology, enhances privacy by wiping user data after every reboot, offering an additional layer of protection.
Customer Support and Additional Features: Surfshark goes above and beyond in terms of customer support, offering 24/7 live chat assistance alongside comprehensive FAQs and application assistance. Users can rely on prompt and knowledgeable support whenever needed.
Notably, its unique selling points include a 30-day Surfshark free trial, unlimited simultaneous connections, and user-friendly apps for a wide range of devices, including routers, Linux, Windows, Mac OS, Android, Firestick, iOS, and smart TVs. The inclusion of features like static IPs further adds to the VPN’s versatility.
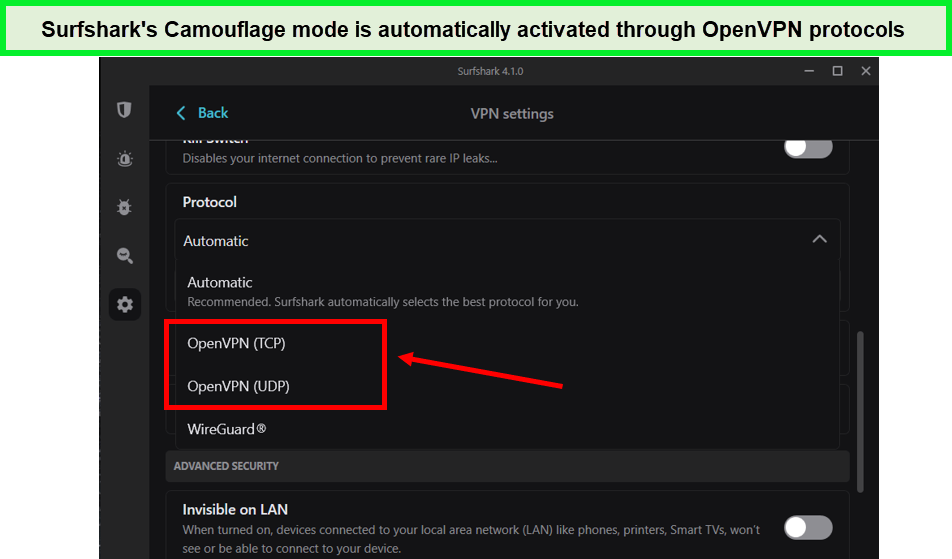
Camouflage Mode:
When it comes to VPN usage, one potential challenge is having your data packets scrutinized by those with network access, potentially exposing your VPN usage. This issue is particularly critical in countries with strict VPN restrictions. Surfshark addresses this concern with its clever solution known as Camouflage Mode, a feature that expertly conceals your VPN activity.
Camouflage Mode, also referred to as obfuscation, works by transforming your internet traffic to closely resemble regular network activity. This ingenious approach ensures that no one can detect you’re using a VPN, providing an extra layer of protection for those navigating the challenges of restricted countries.
Surfshark’s Camouflage Mode serves as a vital tool for users seeking the utmost privacy and anonymity. By disguising your VPN connection, Surfshark makes it nearly impossible for anyone to discern that you’re employing a VPN, effectively bypassing potential VPN detection mechanisms. With Camouflage Mode, Surfshark empowers users to navigate the internet freely and securely, regardless of geographic restrictions.
We applaud Surfshark for integrating such a valuable feature into their VPN service. Camouflage Mode is a testament to their dedication to ensuring user privacy and their commitment to overcoming VPN detection challenges. By enabling users to blend seamlessly into the digital landscape, Surfshark continues to solidify its position as a top-tier VPN provider.
Additional security features
When it comes to security, Surfshark goes above and beyond to offer a comprehensive suite of features that bolster your online defenses. These additional security measures provide peace of mind and further strengthen Surfshark’s position as a top-tier VPN provider.
- Dedicated IP: Surfshark offers the option to purchase a dedicated IP address, providing an extra layer of personalization and control over your online presence. This feature allows you to maintain a consistent IP address, ensuring seamless access to restricted networks or services that require whitelisting.
- Whitelisting: With Surfshark’s whitelisting feature, you have full control over who can communicate with your device. By selectively allowing specific email and IP addresses, websites, and applications, you can maintain a tight circle of trust while effectively blocking all others. This level of control empowers you to safeguard your online interactions and bolster your security posture.
- Military-Grade Security: Surfshark leverages robust security protocols to safeguard your data. You have the flexibility to choose between WireGuard, OpenVPN, and IKEv2, allowing you to select the protocol that best suits your needs. With 256-bit encryption combined with perfect forward secrecy, Surfshark ensures that your data remains impenetrable even if an encryption key is compromised.
- Kill Switch: The inclusion of a kill switch and DNS/IP leak protection adds an extra layer of security, guaranteeing that your online activities remain confidential. In our thorough testing, we have repeatedly examined eight servers for leaks and have not encountered any issues, further solidifying Surfshark’s commitment to watertight security.
- GPS Override (Android Only): Surfshark offers a unique GPS override feature exclusively for Android users. This intelligent functionality automatically matches your phone’s GPS location to the VPN server location you’re connected to. By doing so, Surfshark enables you to utilize location-specific apps or block unnecessary tracking from apps that don’t require your location. This feature ensures that your privacy is maintained while still enjoying the full functionality of location-based services.
We commend Surfshark for its dedication to providing comprehensive security features. The option for a dedicated IP, the granular control of whitelisting, and the utilization of military-grade security protocols all contribute to a robust defense against potential threats. With Surfshark, your online activities remain confidential, protected, and under your control.
Support and Refund Policies of Surfshark
One area where Surfshark truly shines is in its prompt and efficient customer support. The Surfshark customer support team is available round the clock, offering assistance through various channels, including live chat, email, and an extensive knowledge base. Users can trust Surfshark’s customer support to promptly address their queries, provide troubleshooting guidance, and offer support in setting up and optimizing the VPN service.
During our evaluation of Surfshark, we were pleased to receive an immediate response within seconds when we posed a simple question to their support agent. This level of responsiveness reflects Surfshark’s commitment to providing exceptional customer service. In addition to their live chat support, Surfshark’s website hosts a comprehensive Help section, featuring troubleshooting guides, installation tutorials for popular devices, and a wealth of helpful FAQs. This resourceful knowledge base empowers users to find solutions independently, further enhancing their overall experience with Surfshark.
Surfshark offers a 30-day money-back guarantee, allowing users to try the service risk-free for a full month. However, it is important to note that there are exceptions to this policy. Users who have subscribed to Surfshark through platforms such as App Store, Amazon, or iTunes, as well as those who have made payments with gift cards, may not be eligible for a refund after canceling their Surfshark subscription. In such cases, users will need to contact the specific store for refund inquiries. A notable aspect of Surfshark’s refund policy is its willingness to refund payments made with cryptocurrency, setting them apart from many other VPN providers. Users who have paid with cryptocurrency will receive an equivalent amount in US dollars based on the exchange rate at the time of the refund.
During our testing, we received a confirmation email regarding the cancellation within 2 hours, and the refund was processed and received on the 8th day. This demonstrates Surfshark’s commitment to honoring its refund policy promptly. Overall, Surfshark’s refund policy is generous and user-friendly, ensuring customer satisfaction and providing a risk-free opportunity to experience their service.
Surfshark offers a 7-day free VPN trial specifically for Android, iOS, and macOS platforms. This trial period allows users to thoroughly test the service, explore its features, and assess its suitability before making a commitment. Additionally, for users who subscribe on other platforms, Surfshark offers a 30-day money-back guarantee, ensuring that users have ample time to evaluate the service and request a refund if they are unsatisfied. This combination of a free trial and a money-back guarantee underscores Surfshark’s commitment to user satisfaction and reinforces their confidence in the quality of their VPN service.
To receive more insights into the provider, read this detailed Surfshark review!
- Supports unlimited devices for your convenience.
- Expanded coverage to over 100 countries with a recent update.
- Offers great value considering the impressive features.
- Best VPN 2024 for a seamless streaming experience
- Substantial price increases after the initial term.
- Customer support could be more comprehensive.
3. NordVPN – Best VPN for Security
Key Features
- Best VPN for security, streaming, and unblocking geo-restricted content
- 6000+ servers in 61+ countries
- Ultra-fast server connection speeds
- 6 device connections simultaneously
- Price: US$ 3.99 /mo - Save up to 63% with exclusive 2-year plan + 3 months free for a friend with a 30-day money-back policy
- 24/7 live chat support
NordVPN is the best VPN with robust security features. As a major player in the VPN industry, NordVPN effortlessly combines high-speed performance with a wide range of features. It’s an exceptional choice that caters to all customer needs, delivering an effortless and secure VPN experience.
With its privacy-friendly jurisdiction, NordVPN provides all the essential security and privacy features users expect, along with noteworthy extras like double-hop VPN and Onion over VPN. While not the cheapest option available, NordVPN’s robust capabilities make it a compelling choice for those seeking a top-tier VPN service.
| Does NordVPN have the following features? | |
|---|---|
| Multihop | Yes |
| Dark web monitor | Yes |
| Kill switch | Yes |
| Split-tunneling | Yes |
| Can unblock Netflix? | Yes |
| Torrenting | Yes |
Why we selected NordVPN
Established in 2012 and based in Panama, NordVPN has solidified its position as one of the best VPN providers, offering maximum privacy and security online. This VPN provider has earned our trust, as it has never been implicated in logging user data. Additionally, NordVPN has undergone security audits, further assuring users of their safety. We appreciate NordVPN’s dedication to transparency and its commitment to maintaining user privacy. In fact, NordVPN has aced two audits, demonstrating its ongoing commitment to user security. To further instill confidence, NordVPN even offers a free trial, allowing users to experience the service before making a commitment.
Servers and Countries: As of 2024, NordVPN boasts an impressive network of over 6000+ servers in 61+ countries worldwide. This extensive server network allows users to enjoy remarkable speeds, with an average download speed of 82.22 Mbps and an upload speed of 80.19 Mbps. This makes it one of the fastest VPNs in the industry. NordVPN’s global reach ensures that users have a wide range of server options to choose from, providing optimal performance and flexibility.
| Country | NordVPN Locations |
|---|---|
| France | 160 |
| United Kingdom | 440 |
| United States | 1804 |
| Canada | 480 |
| Australia | 220 |
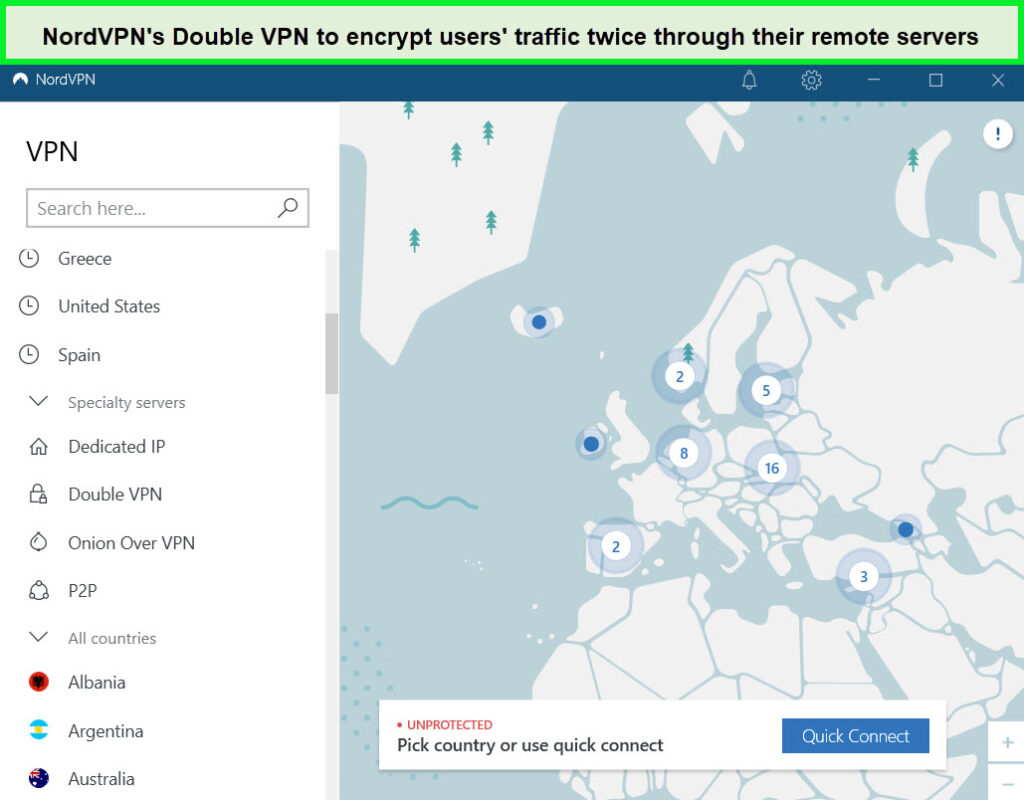
Double VPN and Specialty Servers: One of NordVPN’s standout features is its double VPN capability, allowing users to route their internet traffic through two different VPN servers for added encryption and anonymity. This feature enhances security, making it incredibly difficult for anyone to trace your online activities back to your IP address.
Additionally, NordVPN offers specialty servers tailored to specific needs, including the ability to easily unblock popular streaming platforms like Netflix with NordVPN. Users can conveniently search for the desired server in the navigation bar, making NordVPN an excellent choice for streaming enthusiasts. As per our testing, it is one of the best VPNs for BBC iPlayer, unblocking all the content in one go. We also had the pleasure of streaming Disney+ with NordVPN, as we didn’t get any errors or buffers during streaming. Furthermore, NordVPN is compatible with Kodi, expanding its versatility across various devices and platforms.
Torrenting and Security: You will be ensured a secure environment for torrenting with NordVPN, providing reliable and fast connections for downloading and uploading files. The service guarantees that users remain free from WebRTC/DNS/IP address leaks, offering robust protection for privacy-conscious torrenting. NordVPN utilizes a combination of physical and virtual locations, further enhancing anonymity. With AES-256 encryption, an RSA-4096 key, and SHA384 hash authentication, NordVPN employs top-notch security protocols to safeguard user data. OpenVPN and NordLynx (based on WireGuard) are the VPN protocols of choice, providing a solid foundation for privacy and encryption.
Innovation and Speed: NordVPN has emerged as an innovative VPN provider, earning recognition on TIME’s Best Inventions of 2024 list. We admire NordVPN’s ability to strike a balance between high-quality security and privacy without compromising internet speed. During our rigorous testing, NordVPN consistently demonstrated impressive speeds, reinforcing its position as a reliable and efficient VPN solution.
Premium Features: NordVPN stands out in an oversaturated VPN market, thanks to its robust privacy and security features. With advanced encryption, top-notch VPN protocols, and additional features like Threat Protection and Meshnet, NordVPN offers more than just a VPN service. It has earned our trust through its unwavering commitment to user privacy and its ability to provide high-quality security without sacrificing speed. NordVPN is a powerhouse that continues to deliver exceptional performance, making it a top contender in the VPN industry.
Open VPN and Nordlynx
When it comes to VPNs, the choice of protocol plays a crucial role in determining performance, security, and reliability. NordVPN shines in this regard by offering not one, but two exceptional VPN protocols: OpenVPN and NordLynx, based on the innovative WireGuard protocol.
| Protocol | Speed | Encryption | Data Overhead |
|---|---|---|---|
| OpenVPN | Up to 400 Mbps | Flexible encryption via OpenSSL | Adds up to 20% overhead data usage |
| NordLynx (based on WireGuard) | Up to 1,200 Mbps | Non-flexible (ChaCha 20 only) | Adds up to 4% overhead data usage |
OpenVPN has long been a favorite among users due to its well-balanced blend of security and speed. As an open-source protocol, it has benefitted from continuous community contributions, resulting in ongoing improvements and optimizations. NordVPN’s inclusion of OpenVPN allows users to enjoy a tried-and-tested protocol that offers reliable performance and robust security.
WireGuard, on the other hand, represents the future of VPN protocols. It is a newer, highly efficient protocol that minimizes overhead bandwidth while maintaining top-notch security and impressive speed. NordVPN recognized the potential of WireGuard and introduced its own implementation called NordLynx. By leveraging the strengths of WireGuard while addressing its limitations, NordLynx promises an exceptional VPN experience.
NordLynx takes WireGuard’s efficiency to the next level, allowing users to enjoy remarkable speeds without compromising security. This innovative protocol has been carefully fine-tuned by NordVPN to provide optimal performance, seamless connectivity, and ironclad encryption. By adopting NordLynx, NordVPN demonstrates its commitment to embracing cutting-edge technologies and ensuring that users have access to the most advanced VPN protocols available.
Intuitive Security Features
NordVPN sets the bar high with an array of remarkable security features that go beyond traditional VPN offerings. Their Threat Protection feature stands out by effectively blocking malicious sites, ads, and phishing attempts, even when the VPN is not connected. During our extensive testing, we were consistently impressed by its ability to eliminate all ads on ad-heavy websites like allrecipes.com, providing a clean and secure browsing experience.
Dark Web Monitor is another valuable addition to NordVPN’s security arsenal. This feature promptly alerts you if your VPN-linked email address is compromised on the dark web, allowing you to take immediate action to protect your online identity. Additionally, NordVPN’s Meshnet feature enables encrypted connections between various devices, ensuring seamless access to files and folders across different platforms.
NordVPN takes privacy seriously and offers a range of additional security features to safeguard user data. The inclusion of multi-hop and obfuscated servers enhances data protection by making it harder for prying eyes to intercept your information. These features are invaluable in overcoming firewalls and preserving your privacy.
Speaking of privacy, NordVPN’s no-logs policy has been verified three times, with the most recent audit conducted by Deloitte in 2024 confirming its 100% compliance. The VPN provider’s commitment to privacy extends to its use of RAM-based servers and its location in Panama, a country with no data retention laws. It is clearly the best no-logs VPN, ensuring your online activities remain private and secure.
To bolster security, NordVPN offers essential features such as a kill switch with two settings, 256-bit encryption, and DNS/IP leak protection. Additionally, the VPN provider runs its own DNS servers, ensuring that your online activities cannot be traced back to you.
NordVPN delivers exceptional streaming capabilities, thanks to its built-in SmartPlay feature. We have consistently experienced seamless access to popular streaming sites, including Netflix (in multiple countries), BBC iPlayer, Max (formerly HBO Max), and Hulu. The VPN’s P2P-optimized servers located across various countries enable hassle-free torrenting. Even if you connect to a server that doesn’t support torrenting, it automatically redirects you to a server that does, ensuring uninterrupted P2P file sharing through the NordVPN Windows app or even Linux.
In terms of performance, NordVPN’s speed-optimized NordLynx protocol facilitates smooth streaming and downloading. Our UK speed tests revealed an average loss of just 6% across the three servers tested, showcasing exceptional speed retention for nearby connections. Even with long-distance servers, the average speed loss came to a commendable 19%, making it the best VPN 2024.
Support and Refund Policies of NordVPN
NordVPN may not offer a free trial, but they provide a 30-day money-back guarantee with every subscription. This guarantee ensures that customers have ample time to assess the service and request a refund if they are not satisfied. It’s worth noting that the refund policy applies as long as the initial payment is not older than 30 days. While NordVPN does not offer a completely free service, Android users can take advantage of a 7-day free trial available exclusively on the Google Play Store. It’s important to remember that this trial is provided by Google Play, and certain Terms and Conditions apply. Unfortunately, this trial is not applicable to NordVPN iPhone users.
To request a refund, customers can contact NordVPN’s support team via email at support@nordvpn.com, ensuring that they include “Request for refund” in the subject line. Details such as the associated email address or username, date of purchase, the amount paid, and the reason for cancellation (optional) should be included in the email. Alternatively, customers can utilize NordVPN’s live chat support to cancel their subscriptions and request a refund.
NordVPN’s customer support is exemplary, offering fast and reliable assistance 24/7 through multiple channels. Users can access live chat support, and email support via support@nordvpn.com, or explore the comprehensive knowledge base featuring support articles and helpful FAQs. During our evaluation, we found their live chat support to be impressively prompt, with a response received within 30 seconds when we inquired about their service in the China region.
In addition to the reliable support channels, NordVPN’s website hosts a detailed help section featuring troubleshooting guides, installation tutorials for popular devices, and a wealth of FAQs. This resourceful knowledge base further empowers users to find solutions independently.
To receive more insights into the provider, read this detailed NordVPN review!
- Strong emphasis on security and privacy.
- Flawless performance for streaming purposes.
- The NordLynx feature provides impressive connection speeds.
- An extensive network of servers for reliable and diverse options.
- Steep renewal prices.
4. CyberGhost – Best VPN Service for Unblocking geo-restricted content
Key Features
- Best VPN for unblocking geo-restricted content
- 7900 servers in 100 countries
- Ultra-fast server connection speeds
- 7 device connections simultaneously
- Price: US$ 2.03 /mo - Save up to 84% with exclusive 2-year plans + 4 months free with a 30-day money-back policy
- 24/7 live chat support
CyberGhost is the best VPN Service for unblocking geo-restricted content and continues to impress with its extensive range of competitive features. Our comprehensive review last year included rigorous speed testing, security verification, and meticulous analysis of its privacy tools. Since then, CyberGhost has expanded its server network and is poised to introduce new privacy features while remaining one of the most affordable VPN options available.
The user-friendly applications have been a favorite of ours for some time, striking the perfect balance between simplicity and functionality. With convenient buttons for streaming, torrenting, securing Wi-Fi, and evading censorship, navigating and customizing your VPN experience is a breeze.
CyberGhost’s commitment to comprehensive features is evident in its suite of privacy tools. Whether you want to stream, torrent, secure Wi-Fi, or bypass censorship, CyberGhost has you covered. The feature-loaded and user-friendly interface ensures even beginners can enhance their online privacy and security effortlessly.
Furthermore, CyberGhost stands out as a cost-effective VPN solution. Despite its impressive features and robust server network, it remains competitively priced, making it an appealing choice for budget-conscious users. The value for money, combined with its user-friendly interface, has solidified CyberGhost’s position as a firm favorite among millions of subscribers.
Why we selected CyberGhost
We selected CyberGhost because of its remarkable unblocking capabilities with various websites. Established in 2011 and headquartered in Romania, CyberGhost is a VPN provider that excels in unblocking Video on Demand services and effortlessly bypassing geo-restrictions on any website, regardless of your location. Its efficiency against geo-walls was evident through CyberGhost with Netflix test, allowing easy access to the website without any errors. Moreover, it can easily be qualified as the best Hulu VPN, providing excellent results with its Hulu-optimized streaming server.
One aspect that we appreciate about CyberGhost is its commitment to user privacy. The provider has never been implicated in any data logging controversies and was one of the pioneers in conducting audits back in 2012, ensuring a high level of transparency and trustworthiness.
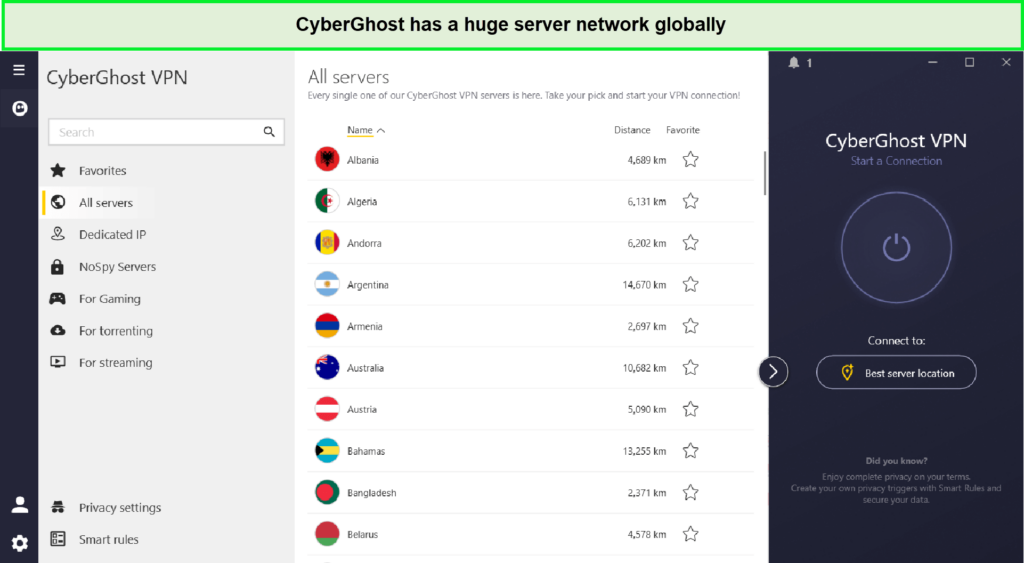
When it comes to server coverage, CyberGhost boasts one of the largest networks of servers worldwide, delivering impressive speeds with an average of 82.22 Mbps in downloads and 80.19 Mbps in uploads. With over 7900 in 100, CyberGhost ensures that users can easily connect and enjoy a seamless browsing experience no matter where they are located.
| Country | CyberGhost Locations |
|---|---|
| France | 777 |
| United Kingdom | 440 |
| United States | 1140 |
| Canada | 550 |
| Australia | 3 |
We particularly like CyberGhost’s specialty servers tailored to specific needs. The provider conveniently categorizes servers based on the channels or services you wish to unblock. For example, if you want to access Netflix, you can simply search for it in the navigation bar, making it hassle-free to enjoy your favorite streaming content.
CyberGhost prioritizes user privacy and security. The VPN is free from WebRTC, DNS, and IP address leaks, employing a combination of physical and virtual server locations to safeguard user data. It utilizes robust AES-256 ciphers with an RSA-4096 key and SHA384 for hash authentication, ensuring a secure and encrypted connection.
While we tested CyberGhost primarily in the United States, the extensive server network spanning 91 countries assures a smooth and reliable connection no matter where you are located. Furthermore, being based in Romania, a country with minimal data retention laws and outside the reach of international surveillance networks, CyberGhost offers an attractive level of privacy protection.
However, one area where CyberGhost could improve is its speed performance. While the overall speeds are impressive, we noticed occasional fluctuations that affected the consistency of the connection. Although this did not significantly impact the browsing experience, we believe there is room for enhancement in this aspect.
Cyberghost No Spy servers
CyberGhost, much like the other VPNs we feature on our website, prioritizes user privacy and ensures that no logs of users’ browsing data are kept. However, CyberGhost goes above and beyond by offering an additional layer of protection through its NoSpy servers. These servers, exclusively operated by CyberGhost in Romania, reside outside the jurisdiction of the 14 Eyes alliance.
Romania’s VPN-friendly laws contribute to CyberGhost’s robust privacy measures, as the country does not mandate data gathering or engage in mass surveillance practices like some others. By connecting to one of CyberGhost’s NoSpy servers, users can have peace of mind knowing that their data remains secure and protected.
CyberGhost NoSpy servers provide guaranteed privacy to users seeking an extra layer of assurance when it comes to their online activities.
Privacy and Security
When it comes to safeguarding your data, CyberGhost truly goes above and beyond. With a range of unique privacy and security features, we know we can rely on CyberGhost to protect us whether we’re connected to public Wi-Fi, defending against malware, or requiring an extra layer of privacy for sensitive online activities.
CyberGhost stands out with its comprehensive set of security and privacy features:
- Romanian base and NoSpy servers: Operating outside the jurisdiction of the 14 Eyes Alliance, CyberGhost’s headquarters in Romania provide an added layer of protection. The company’s exclusive NoSpy servers, managed solely by CyberGhost employees, minimize the risk of data interception, further ensuring your online privacy.
- Customizable protection: CyberGhost offers versatile protection options, including the Block Content feature that effectively prevents ads, trackers, and malware. Smart Rules allows you to customize how and when the app protects your traffic, providing enhanced security on public Wi-Fi. Additionally, Smart Rules enables you to set exceptions for specific apps and websites, allowing for more flexibility through features like split tunneling.
- Quality protocols: CyberGhost offers a selection of reliable protocols, including IKEv2, L2TP/IPSec, OpenVPN, and WireGuard. It’s worth noting that OpenVPN is not available for iOS or macOS devices, which may be a drawback for users of those platforms.
- Dedicated IP option: For a small monthly fee, CyberGhost provides the option to acquire a dedicated IP address. This personalized IP address ensures that you avoid overcrowding and prevents websites from detecting your connection as originating from a VPN. Dedicated IPs are available in the US, the UK, Canada, Germany, and France.
- Dependable privacy protection: CyberGhost’s strict no-logs policy was audited by Deloitte, verifying that your personal information is never stored. Similar to ExpressVPN, CyberGhost has implemented diskless servers to eliminate any data retention concerns, ensuring your data remains secure.
- Security essentials: With 256-bit encryption and perfect forward secrecy, CyberGhost guarantees robust protection for your personal data. DNS/IP leak protection and a kill switch further enhance your online security, providing a reliable defense against potential threats.
- User Experience: Beyond its impressive security measures, CyberGhost also excels in user experience. Its easy-to-use apps and speedy connections contribute to a seamless browsing experience. Whether you’re a beginner or an experienced VPN user, CyberGhost’s intuitive interface and fast connections make it a pleasure to use.
While CyberGhost offers an array of impressive features, there are a couple of areas where we believe it could improve. Firstly, the unavailability of OpenVPN for iOS and macOS devices may limit the protocol options for users on those platforms. Additionally, the availability of dedicated IP addresses in more countries would be beneficial to users seeking a personalized connection experience, which also makes this provider the best VPN with Dedicated IPs.
Plans and Moneyback Guarantee
CyberGhost stands out for its affordability, offering plans that won’t break the bank. What’s even better is that you can try out all of its features with a 24-hour free trial. However, since fully testing a VPN requires more time, we recommend taking advantage of CyberGhost’s 45-day money-back guarantee. This extended refund period is available with all long-term plans, providing ample time to explore and evaluate the service.
To check the reliability of CyberGhost’s refund policy, we conducted our own testing. Similar to ExpressVPN, CyberGhost offers 24/7 live support, and we found their customer service to be friendly and knowledgeable. With a generous 45-day money-back guarantee on all plans longer than the 1-month plan, you can try out CyberGhost VPN risk-free and request a full refund within 45 days. While most VPNs typically offer a 30-day money-back guarantee, we were impressed by CyberGhost’s extended period.
Although CyberGhost also provides a 1-day free trial for Mac and Windows, this limited time frame may not be sufficient for a thorough evaluation. However, its compatibility with complicated OS makes it one of the best VPNs for Mac.
Customer support plays a crucial role in the VPN experience, and CyberGhost excels in this area. With various support options available, including 24/7 live chat, email support, comprehensive guides, and FAQs, CyberGhost strives to meet users’ expectations. The extensive collection of guides and FAQs ensures that users have access to the information they need for installation and usage. Additionally, if further assistance is required, users can submit a ticket to receive personalized troubleshooting support.
If you want a VPN for private browsing that unblocks all websites smoothly, CyberGhost is definitely a great choice. A commitment of 3 years will reduce the costs from $12.99 to US$ 2.03 /mo - Save up to 84% with exclusive 2-year plans + 4 months free.
To receive more insights into the provider, read this detailed CyberGhost review!
- Vast selection of servers available.
- Apps packed with advanced features.
- Impressive speeds with the WireGuard protocol.
- Convenient streaming features to enhance the experience
- App updates are infrequent.
- UK Netflix and Disney+ are not accessible.
5. Private Internet Access – Best VPN Choice for Beginners
Key Features
- Best VPN for torrenting to unblock geo-restricted content
- 35000+ servers in 84 countries
- Ultra-fast server connection speeds
- Unlimited device connections simultaneously
- Price: $3.99/mo with a 30-day money-back policy
- 24/7 live chat support
Private Internet Access (PIA) stands out as the ultimate VPN for torrenting. While it may not be the absolute fastest, cheapest, or most robust VPN option out there, PIA has an undeniable appeal with its impressive range of features and an astonishing number of servers. If you’re looking to enhance your online privacy and security, especially for torrenting, PIA is our top pick for 2024.
With great speeds, top-notch security measures, and 24/7 live chat support, PIA caters to both seasoned VPN users and newcomers in the realm of online privacy.
PIA offers excellent value for your money, thanks to its global server network and the utilization of protocols like WireGuard to ensure speedy connections. While it is reliable and secure, the user interface could use a facelift to enhance its aesthetics and functionality. With improvements in these areas, PIA has the potential to become a leading competitor in the VPN market.
Why we selected Private Internet Access
PIA boasts an extensive network of over 35,000 servers in 84+ locations, positioning itself as a formidable option for streaming, torrenting, and gaming. While its server count may be slightly lower than some providers, PIA’s optimized servers ensure a seamless and uninterrupted experience when accessing your favorite content.
| Country | PIA Locations |
|---|---|
| France | 4 |
| United Kingdom | 4 |
| United States | 158 |
| Canada | 4 |
| Australia | 6 |
We commend PIA for its robust security measures, including AES-256 encryption, a powerful kill switch, and DNS/IPv6 leak protection. The ability to connect unlimited devices with a single account offers unparalleled flexibility and convenience for users.
In terms of privacy, PIA strictly adheres to a no-logs policy and operates its entire server network, instilling an additional layer of trust.
Although PIA does not offer a free trial, they provide a 30-day money-back guarantee, allowing users to test the service without financial risk. That being said, throughout our review, we found PIA to offer reasonable pricing, delivering good value for its overall performance.
PIA VPN performed admirably in terms of speed and reliability, particularly on local servers. It effectively bypassed restrictions on popular streaming services like Netflix, Hulu, Amazon Prime, and BBC iPlayer. In fact, it’s the best MLB TV VPN, providing consistent connection throughout our live streaming.
With dedicated apps for major platforms, PIA ensures compatibility with iOS, macOS, Android, Windows, and FireStick devices. Its user-friendly interface caters to both beginners and advanced users, excelling in bypassing censorship and accessing geo-restricted websites.
When it comes to customer support, PIA provides multiple avenues for addressing user inquiries, ensuring a satisfactory experience.
While PIA has its strengths, including optimized servers and strong security features, further expansion of its server network and potential improvements in pricing plans would solidify its competitiveness in the market.
Advanced Split Tunneling
Split tunneling is a feature that often goes unnoticed, but we believe it plays a crucial role in enhancing the VPN experience. PIA not only recognizes the importance of split tunneling but also goes above and beyond to provide advanced customization options for both apps and websites. With PIA’s split tunneling feature, users can multitask, access VPN-restricted websites, establish remote work connections, and even bypass the VPN for specific hosts.
What we particularly appreciate about PIA’s split tunneling is its ability to automatically bypass the VPN connection when visiting websites that block VPN IP addresses. This intelligent functionality ensures a seamless workflow without the hassle of constantly enabling and disabling the VPN. PIA empowers users by giving them greater control and flexibility over their online activities, allowing them to tailor their VPN usage to their specific needs.
Security Features and Encryption options
PIA stands out with its fully customizable security features, allowing users to tailor their connection according to their preferences. The choice between OpenVPN and WireGuard protocols offers versatility. During our speed tests, WireGuard demonstrated superior performance, outperforming OpenVPN by 9% for seamless streaming experiences.
| Encryption Options | VPN Protocol Options |
|---|---|
| 128-bit AES | OpenVPN |
| 256-bit AES | WireGuard |
| 256-bit AES with GMC | IPSec |
For those concerned about the security of their bank accounts and confidential information, PIA’s support for the highly secure OpenVPN protocol is commendable. Additionally, the option to select encryption levels, ranging from 128-bit to the robust 256-bit, adds an extra layer of protection.
PIA goes beyond standard security measures by offering additional layers of protection. The built-in MACE ad and malware blocker enhance online safety. The option to enable “Multi-Hop” allows users to route their connection through a SOCKS5 or Shadowsocks obfuscation proxy alongside the VPN server. However, it’s worth noting that this feature may not work in China, unlike some VPNs with obfuscation capabilities.
To mitigate the risk of third-party interference, PIA has introduced NextGen servers. These self-owned colocated servers are strategically located in North America, Europe, and Australia, ensuring enhanced security and reliability.
In terms of essential security features, PIA offers leak protection and an adjustable kill switch. The kill switch prevents any data leaks, even when the VPN is manually disabled. During our tests, we found no leaks, reaffirming PIA’s commitment to data security.
PIA also provides a proxy browser extension, available for free on Chrome, Firefox, and Opera. While the extension doesn’t encrypt traffic like a VPN, it allows users to change their virtual location.
PIA’s court-proven no-logs policy provides peace of mind. It has repeatedly demonstrated its commitment to user privacy, even when faced with demands for user data. This is particularly reassuring considering PIA’s US-based jurisdiction, which falls within the scope of the 14 Eyes Alliances.
Overall, PIA offers a robust and highly customizable security suite. However, we believe that continuous innovation and expansion of server locations could further enhance its competitive edge in the VPN market.
Customer Support and Resources
PIA’s user-friendly apps make installation a breeze, and the inclusion of a smart DNS feature adds convenience. A standout feature is the availability of a native GUI app for Linux, catering to a wider range of users. In case of any assistance, PIA offers customer support through live chat and boasts an extensive knowledge base comprising FAQs, tutorials, and setup guides.
One of the highlights of PIA is its affordability, with plans starting at just $2.03 per month. This makes it one of the most cost-effective options on our list. Furthermore, all plans are backed by a reliable 30-day money-back guarantee, allowing users to test PIA without any risk. PIA’s 24/7 live chat support is readily available to expedite the refund process.
During our evaluation of PIA’s live chat support, we found it to be efficient and informative, with a response rate of approximately 80%. In the event that you don’t receive an immediate answer, PIA encourages users to utilize their ticketing system by emailing their queries.
For our PIA VPN review, we tested their 24/7 live chat support and initially interacted with a chatbot. However, upon request to speak with an agent, we were promptly connected to a human representative within 4-5 minutes. Our question regarding supported Netflix libraries received an informative response within seconds.
In terms of the ticketing system, we received a response from PIA’s customer support representatives within approximately 8 hours. Additionally, their website features a comprehensive knowledge base with over 100 FAQs, regularly updated to address common issues.
To provide further assistance, PIA VPN maintains a dedicated Twitter account to address user queries. While our query about a technical app issue was met with a response after two days, it’s worth noting that quick resolutions may vary.
If you’re looking for a VPN service that’s easy to use and comes with great 24/7 customer support, PIA is the best choice.
To receive more insights into the provider, read this detailed PIA review!
- Provides outstanding value for the price.
- Successfully unblocks US Netflix.
- Offers reliable apps with a kill switch feature.
- Passed a no-log audit, ensuring privacy and security.
- Apps are feature-rich but may have a steep learning curve.
- A full app audit is currently being developed.
6. IPVanish – Best VPN for Beginners
Key Features
- Easy-to-use interface
- 2200+ servers in 75+ locations
- Ultra-fast server connections
- Unlimited device connections simultaneously
- Price: $2.92/mo with a 30-day money-back policy
- 24/7 live chat support
IPVanish is a great VPN for beginners and experts alike offering a super interactive and convenient interface to use. The features are easily accessible with proper categorization in the app. Moreover, it brings a well-designed and simple structure that is easily operable by first-time users.
IPVanish has a network of over 2200 servers spread in 75+ locations worldwide. You can easily connect to countries like Australia, Finland, Canada, Italy, Portugal, France, Spain, the United Kingdom, and more with this VPN.
Why we selected IPVanish
We selected IPVanish because of its intuitive apps and excellent services. IPVanish passed our test and ranked amongst the top ten VPNs for online activities. It is currently available at an extremely reasonable price with 75% off for a limited time at $2.92/month.
Our favorite feature offered by IPVanish is the unlimited number of devices that can be connected simultaneously under a single account. We loved the idea of how you can purchase it once and use it on as many devices as you want for performing different activities online covered with VPN protection.
In terms of speed, it brings ultra-fast speed connections that allow unrestricted online access. With its high-speed servers, you can instantly connect to any one of the 75+ locations offered by the VPN. Moreover, we have analyzed the performance of its servers and are satisfied with the results.
IPVanish is a good choice for streaming blocked content across the globe. You can unlock nearly all major streaming platforms like Netflix, ESPN+, Hulu, and many more. Furthermore, the unlimited bandwidth lets you enjoy your favorite streams without any bounds. You can also use IPVanish for high-speed torrenting to download heavy files in no time. That’s also the reason why it’s the best VPN for Prime Video, providing access to multiple foreign libraries across the globe.
IPVanish supports Android, Windows, iOS, Mac, Linux, and other different devices, including Fire TV, NVIDIA Shield, and routers. It also provides a browser extension for Chrome so that you can browse in a protected and private environment. Moreover, it provides you with high-end privacy by masking your IP address and assigning you a dummy address to access just anything you want. It especially protects you against Man-In-the-middle attacks and Evil-twin-attacks. It also follows a no-traffic logs policy to ensure zero monitoring.
IPVanish’s privacy and security practices were audited recently by an independent privacy and security auditing company. They confirmed that IPVanish doesn’t log or collect user data and guarantees privacy-conscious services for users.
Moreover, it has a robust server network spread in more than 75 locations worldwide. We have listed the number of locations offered in some popular counties in the table below:
| Countries | Locations |
| UK | 4 |
| USA | 20 |
| Australia | 5 |
| New Zealand | 1 |
| France | 3 |
Kill Switch
If your connection fails abruptly, it could pose serious threats by leaking your original IP address to the source. Your server can be blacklisted making you unable to access the services. Therefore, a kill switch is important for VPNs to prevent accidental privacy leakage. IPVanish offers a kill switch that effectively and efficiently kills all VPN traffic immediately after the VPN connection drops on your device. We like its simplicity which allows users to reconnect the devices with IPVanish.
Robust Customer Support and Money Back Guarantee
No matter how perfect a service is, users can need assistance at any point. Therefore, a responsive and cooperative customer support service is essential for users. IPVanish offers a helping hand for customers with live chat and email support 24/7. Additionally, it offers a service to contact via phone line which is not common in premium VPNs. We are impressed to find the availability of phone call service by IPVanish.
We have listed the details for each service in the table below:
| Customer Support Services | Availability |
|---|---|
| Live chat | 24/7 |
| 24/7 | |
| Phone line | 9 AM – 5 PM CT (UTC-6) Monday – Friday |
In terms of policies, IPVanish brings a 30-day money-back guarantee to give you peace of mind. You can purchase the package of your choice and explore the features and services for 30 days without any pressure. If you are not happy with the services, you can claim a refund by applying for an IPVanish free trial through its website.
The best thing we found about the refund process is that you don’t need to contact customer support for claiming your money. Rather, it is directly done via the account portal on the website.
To receive more insights into the provider, read this detailed IPVanish review!
- Audited privacy policy
- Ultra-fast servers
- Unlimited device connections
- Unblocking and streaming capabilities
- Live chat 24/7 and phone line
- Some Netflix Locations do not work
7. PureVPN – Best VPN with Feature-rich Interface
Key Features
- Feature-rich interface
- 6500+ servers
- Average speed servers
- 10 simultaneous connections
- Price: $2.05 with 75% off and a 31-day refund
- Live chat 24/7
PureVPN is among the ten best VPNs that come with a feature-rich interface. You get several useful features like split tunneling, port forwarding, and obfuscation technology with a focus on user security and privacy.
Based in the British Virgin Islands, PureVPN offers a massive server network comprising over 6500 servers in 70+ countries. You can enjoy PureVPN-protected services in Spain, Germany, the UK, France, Australia, Singapore, Mexico, Japan, United Arab Emirates, the Netherlands, and many more countries around the globe.
With PureVPN, all connectivity needs while traveling have been taken care of. We can easily move to almost any part of the world and access whatever we wish by connecting to the PureVPN servers. And for the very same reason, we have added PureVPN to our list of best VPNs for travel in 2024.
Why we selected PureVPN
We have selected PureVPN because of the versatile features and quality services it offers. We are amazed at the insanely low price at which we can subscribe to PureVPN. It is available for $2.05 at a 75% discount for a limited time.
PureVPN supports 10 device connections simultaneously which are quite generous. Moreover, it offers apps for smartphones, personal computers, routers, etc. It is also compatible with Android, Windows, macOS, Linux, and iOS devices. It’s worth noting that we had no issues installing PureVPN on Firestick, Kodi, Smart TV, Roku, and other streaming devices.
PureVPN servers have average speeds overall. We have tested the performance of its servers at different locations and observed its speed to be slightly lesser than the other premium VPNs assessed. Users even have a list of specialty servers and modes for varied needs; streaming, P2P/file sharing, unblocking, dedicated IP, etc. The best part of all: the VPN follows a no-logs policy, verified by the security firm, Altius IT in a PureVPN audit report.
For streaming with PureVPN, you can experience HD and 4K Ultra HD servers. Moreover, unlimited bandwidth prevents ISP throttling so you enjoy unrestricted streaming. You can watch Netflix and Hulu with PureVPN by unlocking many different libraries from different countries. We also had a great experience streaming BBC iPlayer with PureVPN, recording no buffers whatsoever.
PureVPN is a good choice for torrenting activities offering P2P-optimized servers. However, it restricts torrenting in countries that don’t allow the practice, such as Japan.
In terms of server networks, PureVPN has one of the largest networks among the premium VPNs. You can find servers in 70+ countries across the globe. All of its servers displayed reasonable speeds during our PureVPN speed test.
For support, you have a 24/7 responsive live chat, and features include NAT Firewall, Split Tunneling, Ad/Tracker blocking, IPv6 Leak Protection, Port Forwarding, Kill Switch, DDoS Protection, and dedicated IPs.
| Countries | Locations and servers |
| UK | Glasgow, London, Manchester |
| USA | Ashburn, Atlanta, Chicago, Houston, Miami, Los Angeles, New Jersey, Phoenix, New York |
| Australia | Brisbane, Sydney, Perth, Melbourne |
| New Zealand | |
| France | Paris, Roubaix |
Strict Logging Policy
In terms of privacy protection, we learned that PureVPN follows a no-logs strategy, and hides our original IP address, as well as our complete browsing history. All our activities are covered while we enjoy the platform, as it is headquartered in a privacy-friendly region.
Furthermore, we noticed that it only collects our name, email address, payment details, and total bandwidth consumption. Also, it uses AES-256-bit encryption to conceal our IP address and all activities on the network.
Dedicated Support and Money Back Guarantee
PureVPN offers live chat support 24/7 and an email service. Its support team is always available to help users in case of queries or issues. You can cancel PureVPN and apply for a refund within 31 days of purchase, which is a slightly longer period than what most premium VPNs offer. The biggest drawback of this provider, and one that makes it one of the very few providers that offer no version of a PureVPN free trial for any duration.
If you are a budget hunter in search of a multifaceted VPN service, there is no better option than PureVPN. It handles all your VPN-related needs, minus the paying of high subscription costs.
To receive more insights into the provider, read this detailed PureVPN review!
- Strong protocol support
- Huge global network
- Based in a privacy-safe country
- P2P-optimized servers
- Military-grade encryption
- No free trial
- Latency on Mac and Windows apps
8. Windscribe – Best Free VPN
Key Features
- Free VPN plan
- Servers in 63 countries and 110 cities
- Fast speed servers
- Unlimited device connections simultaneously
- Price: $5.75/mo with a 3-day money-back policy
- Ticket support system
Windscribe brings both free and premium plans for users. It offers 10 GB of data each month with servers in 10 countries for its free plan users. They can connect to servers in the United Kingdom, France, the United States, Canada, Germany, Hong Kong, the Netherlands, Romina, Turkey, and Switzerland.
In terms of server networks, it provides servers in around 63 countries spread over 110 cities. It doesn’t tell much about the exact number of servers available for users. However, our observation shows its server count to be lesser than most premium VPNs.
Windscribe comes with several unique features, such as Split Personality, Autopilot, and Time Warp that we haven’t found in other VPNs yet. Its ROBERT is an IP-blocking tool that blocks ads, and trackers prevents infections, and personalizes the block list.
Why we selected Windscribe
Windscribe was primarily chosen because of the availability of both free and paid VPN services. The free plan offers limited bandwidth and servers in 10 countries. Whereas the premium plan provides unlimited data with servers in 63 countries.
While assessing Windscribe, we found out its support for unlimited device connections and we couldn’t take it off our list. We could connect just as many devices as we wanted which is truly like offering the best value for money.
You can download Windscribe apps for Android, Windows, MacOS, and Linux devices. Furthermore, it is compatible with Fire TV, routers, and Huawei. You can even use its Chrome and Firefox extensions to enjoy a private browsing experience.
Windscribe claims to provide fast-speed servers. To test these claims, we assessed the performance of its servers at 9 different locations and obtained good speed results.
We were surprised to note its torrenting support on both free and paid plans. Your P2P traffic can flow securely through the network with Windscribe’s torrenting capabilities.
In terms of privacy, we have observed numerous useful features that make Windscribe good for privacy protection. All user traffic is encrypted using AES-256-bit encryption. Moreover, features like kill switch, split tunneling, and port forwarding enhance the user’s protection.
Windscribe promises a no-logs policy guaranteeing no user data is collected, leaked, or misused. On top of this, it comes with perfect forward secrecy and double hop for double encryption and transmission.
| Countries | Locations and servers |
| UK | Edinburgh, London, Manchester – 5 |
| USA | New York, Seattle, San Jose, Santa Clara, Phoenix, Los Angeles, Las Vegas, Orlando, Philadelphia, Washington DC, Detroit, Chicago, Charlotte, Boston, Denver, Kansas City, Atlanta, Dallas – 45 |
| Australia | Brisbane, Sydney, Perth, Melbourne, Adelaide, Canberra – 11 |
| New Zealand | Auckland – 2 |
| France | Paris – 2 |
Optimized worldwide streaming
Windscribe allows streaming with its fast-speed servers like other premium VPNs. However, what makes it prominent in the list is its strong capabilities to deal with the streaming blocks. Thanks to its premium feature called “Windflix,” you can easily access Netflix with Windscribe and explore multiple regional libraries.
With Windscribe Pro, you can also access other popular platforms like Disney+, Hulu, BBC iPlayer, and Amazon Prime Video.
In the case of the free plan, Netflix is no longer supported, but it works with a few Netflix regions, Hulu, HBO Max, etc. Moreover, it can bypass American sports restrictions.
Considering its streaming capabilities, we notice that it needs to improve speed for high-quality and uninterrupted streaming. Additionally, SmartDNS is needed for use on PlayStation, Xbox, etc.
Customer Support and Refund
In terms of customer support, you can contact Windscribe’s team via the ticketing system which is available in a fixed time slot, or email your queries to their mailing address. Secondly, the unavailability of a live chat service was quite disappointing for us.
Windscribe offers a 30-day refund policy for premium plan users to claim their money if they are not satisfied with the services. Again, the refund applicability period is extremely short for users to properly test and try all features in the app.
Anyhow, we hope for the developers and management to consider the concerns and incorporate the requirements.
To receive more insights into the provider, read this detailed Windscribe review.
- Bypasses restrictions in China
- Free plan works for 32 Netflix regions
- Unlimited simultaneous device connections
- Strict no-logging policy
- Unique features
- No live chat service
- Short refund policy
- No Smart DNS
9. TunnelBear – Best UI VPN
Key Features
- User-friendly and Interactive apps
- Over 5000 Servers in 47+ countries
- Fast-speed servers
- Unlimited device connections
- Price: $3.33/mo on a 67% discount with no clear refund policy
- No live chat support
TunnelBear provides highly-interactive apps and a well-designed interface. We liked its forest-themed animated apps and found them super interesting. Its intuitive map is easy to navigate and simple to use. We love the subtle animations of its apps which aren’t available in other VPNs.
TunnelBear offers over 5000 servers in more than 47 countries and 40+ locations. You can connect to a powerful network in Australia, Argentina, Austria, Canada, Germany, France, Italy, Japan, Malaysia, Netherlands, New Zealand, Singapore, Spain, Switzerland, the UK, the USA, and many more countries.
Why we selected TunnelBear
We have selected TunnelBear mainly because of the interactive interface and the free deal it offers. TunnelBear brings a paid and free plan for users, where they can enjoy secure browsing. Its free plan allows up to 2 GB of data whereas the premium plan covers unlimited browsing activities.
We are impressed with the city-level server selection and unlimited device connections available in the premium plan. You can connect your Android, Mac, and Windows devices with TunnelBear. Moreover, it offers apps for iPhones and iPads to provide online protection.
TunnelBear offers a special Teams plan to cover the needs of businesses with 2+ users. It is packed with premium VPN servers, city-level selection, centralized team billing, and admin & account manager tools. You can pay through Bitcoin, MasterCard, VISA, or American Express.
TunnelBear servers are overall fast in terms of speed in a way that you can perform all speed-intensive activities easily. When we assessed its servers in Australia, Canada, and some other locations, we were totally surprised at the speed test results.
TunnelBear servers generally work for streaming. We tried to unlock US Netflix with it, but we could succeed on the second attempt. However, Hulu and Disney+ got unblocked smoothly, but the performance was below average and slow.
Moving ahead, TunnelBear supports torrenting with its P2P-optimized servers. We tested its torrenting capabilities by downloading small to medium-sized files and received an impressive response.
TunnelBear offers a strong security platform that uses AES-256-bit encryption to secure traffic and mask personal identity. Its GhostBear feature prevents VPN blocking, ISP tracking, and government monitoring. It supports WireGuard and provides Split tunneling, kill switch, and anti-censorship technologies.
| Countries | Locations & Servers |
| USA | Not specified |
| UK | Not specified |
| France | Not specified |
| Australia | Not specified |
| New Zealand | Not specified |
No logging
TunnelBear is an independently-audited VPN framework. In terms of privacy, TunnelBear holds an award-winning privacy policy available on the website. It follows a no-logs policy strictly and doesn’t collect personal user data. It only stores payment information, user account details, OS version, etc. It states zero selling of personally identifiable information.
We are impressed to find its privacy policy extensively discussed on the website. It presents different clauses relevant to user data safety and management. Furthermore, its privacy policy undergoes constant changes, therefore, the updates are posted online.
Free Plan and Customer Support
TunnelBear’s free plan is great for beginners exploring the service. Individuals can use up to 2 GB of data for browsing or any other activities. It is suitable for limited usage or testing purposes.
For customer support and guidance, SupportBears only provides an email channel via which users can report issues or concerns. We are disappointed to note the unavailability of basic support services like live chat.
Another factor that discouraged us was its extremely weak refund policy. TunnelBear mentions handling every refund request on a case-by-case basis. When you contact SupportBears, your refund request is processed and sent for review. It is important to note that not every request gets approved.
To receive more insights into the provider, read this detailed TunnelBear review!
- Beginner-friendly apps
- Annually-audited
- Award-winning privacy policy
- Unlimited simultaneous connections
- Split tunneling doesn’t work on all platforms properly
- No live chat support 24/7
- No clear refund policy
10. VyprVPN – Privacy-friendly VPN
Key Features
- Privacy-friendly and safe
- 700+ servers in 90+ locations
- High-speed servers
- 10 simultaneous device connections
- Price: $5/mo with a 30-day refund
- 24/7 ticketing system
VyprVPN provides a privacy-friendly and trusted platform with its headquarters based in Switzerland. VyprVPN has been offering privacy-focused services for 15 years to eliminate VPN censorship and internet restrictions.
VyprVPN protects your data and activities against trackers and hackers. It provides unparalleled security with powerful servers, hardware, and network. VyprVPN’s VyprDNS is effective against DNS censorship and Man-In-The-Middle attacks. It also lifts censorship from certain websites and services.
In terms of the server network, VyprVPN offers over 700 servers operating in 90+ locations worldwide. You can connect to more than 300,000 IP addresses with VyprVPN. Moreover, its Dynamic server switching prevents unavailability and overloading of servers.
VyprVPN’s Chameleon protocol effectively helps users connect from highly-restricted countries with internet blockages, such as China, India, and The Middle East. It lifts VPN blocking problems and eliminates speed issues caused by bandwidth throttling.
Why we selected VyprVPN
We selected VyprVPN because of its core attention and commitment to privacy. It supports a secure combination of protocols that promote private connections globally.
In terms of pricing, it offers an annual subscription for $5/month and a monthly deal for $10/mo. It covers 10 simultaneous device connections and provides apps for Android, Windows, Mac, and iOS devices. You can also protect your routers by installing VyprVPN for protecting the entire network of devices. It’s also one of best VPNs for Chrome with easy-to-install extensions.
VyprVPN provides a fully verified and publically audited no-log VPN app that ensures zero information collection. Additionally, it ensures public WiFi protection by automatically connecting to the VPN just when you access any unknown network.
VyprVPN provides good-speed connections that enable unrestricted and smooth activities. To verify the performance, we tested its servers and got incredible results overall.
VyprVPN’s servers allow high-speed streaming and great unblocking capabilities. It can effortlessly work with HBO Max, Netflix, Hulu, and many more popular streaming platforms. It easily lifts all geo-restrictions are lifted to make you access the content as local users.
For torrenting, VyprVPN provides a monitoring-free environment with P2P-friendly networks. Based in Switzerland, you can experience smooth and fast downloads. While testing this feature, we were able to torrent a 2.3 GB file in under 7 minutes.
We like the extensively spread server network offered by VyprVPN. You can connect to servers in Canada, the USA, Australia, Germany, France, Netherlands, Turkey, Russia, Egypt, Pakistan, India, Saudi Arabia, United Arab Emirates, and many more countries.
| Countries | Locations and servers |
| USA | Los Angeles, Seattle, Austin, New York City, Miami, Washington D.C, Chicago, San Francisco – 8 |
| UK | London – 1 |
| France | Paris – 1 |
| Australia | Melbourne, Perth, Sydney – 3 |
| New Zealand | Auckland – 1 |
Kill Switch and Split Tunneling
VyprVPN brings an effective kill switch that blocks all traffic automatically after the VPN gets disabled or disconnected all of a sudden. This prevents user identity from leaking on the network and ensures advanced protection and private connection for P2P traffic.
VyprVPN provides split tunneling to divide the traffic load and ensure a normal flow of activities. Furthermore, it offers WebRTC and DNS leak protection and uses military-grade AES-256-bit encryption.
After a thorough analysis, we are satisfied with its security measures and privacy protection. We love its pure dedication to no data collection on the platform being the first independently audited VPN.
Live Chat and Money Back Guarantee
Customer support is critical to the selection of a VPN. Therefore, we pay detailed attention to customer services while assessing the VPN providers. In the case of VyprVPN, users can contact the team only via a ticketing system that is not highly responsive.
VyprVPN doesn’t offer a separate channel for sending emails directly. When we tried to launch the email support, the same ticketing support page was loaded. We prefer getting at least a live chat service available 24/7 to stay in touch with the human agents.
In terms of a money-back policy, VyprVPN offers a 30-day money-back guarantee. You can get a complete refund within 30 days of purchase if you are not satisfied with the services.
To receive more insights into the provider, read this detailed VyprVPN review!
- Audited apps
- Leak protection
- Chameleon technology
- Based in privacy-safe Switzerland
- Servers in restrictive countries
- No live chat service 24/7
- Free trial requires credit card registration
What is a VPN? How VPNs Keep You Safe Online?
A VPN or Virtual Private Network enables users to safeguard all their activities online by creating a private and secure browsing session. Network protection is especially needed when using public Wi-Fi to prevent tracking and eavesdropping on the user’s data and activities.
A VPN builds a safe and encrypted tunnel between a user’s device and the VPN server to conceal their original identity and online activity. VPNs also provide online privacy to bypass ISP tracking and bandwidth throttling by passing entire user traffic via the internet channel of the VPN provider.
No users or internet providers can see what others are doing as all browsing information is completely hidden, making it almost impossible for hackers or trackers to collect or observe online activities.
How Do VPNs Work?
A VPN works by transmitting the internet connection of a device through a private service instead of routing it through their regular ISP. The Virtual Private Network functions as an intermediary between the user who connects to the internet for protection by masking their real location and IP address.
With a VPN, you get a strongly encrypted and fully private tunnel to access the internet on your device while keeping your personal data, address, and all other data hidden. Moreover, all your traffic flows via a safe connection provided by the VPN. Therefore, whatever traffic is sent to the internet is actually redirected to the VPN instead of your device.
When you try to connect to the internet using a VPN, all information from your device is sent to websites via an encrypted channel created by the VPN. This request is then forwarded by the VPN followed by a response from that website which later reaches you.
Can a VPN Track You Online?
Yes, a VPN can track you online as it knows your original IP address, watches what you do online, and probably holds your payment information. Therefore, it is extremely important to select a trustworthy and reliable VPN.
The majority of VPNs claim to store zero logs of user activities online. All top-performing VPN service providers ensure all browsing history is deleted and isn’t left trackable.
The most common user data collected by VPNs include:
- IP address
- Bandwidth consumption
- Name
- Email address
- Payment information
Even though many VPNs are based in countries that legally enforce recording logs, reputable VPNs are headquartered in regions that don’t impose such requirements. You must choose a VPN based in a privacy-friendly zone that doesn’t enforce logging activities.
The Impact of AI on the Future of VPN Technology
AI’s impact on VPN technology heralds a new era of enhanced security and improved performance. Advanced algorithms in AI-driven VPNs enable better threat detection and optimized server selection, ensuring robust security and smoother user experiences. This integration promises to effectively counter sophisticated cyber threats and provide a more adaptive and efficient VPN service.
After comprehensive research, ExpressVPN stands out as the best VPN choice for 2024. Its strengths lie in superior speed, thanks to its proprietary Lightway protocol, and robust security features, including a proven no-logs policy and RAM-based servers. Additionally, its versatility in successfully unblocking streaming services and supporting safe torrenting makes it a top choice for a wide range of VPN users.
How To Choose the Best VPN?
When choosing a VPN, there are a few things you should look for:
- Security and privacy: Choose a VPN with reliable security features and no data leakage, preferably with independent audits and a no-logs policy, a kill switch, and DNS leak protection.
- Speed: Look for a VPN with a proven track record of good performance, especially when connecting to distant servers.
- Strong encryption: Opt for a VPN with next-generation encryption, such as AES-256, to ensure maximum privacy and protection and the ability to unblock popular streaming services like Netflix, BBC iPlayer, Amazon Prime Video, Hulu, or HBO Max, and other geo-restricted content.
- Easy setup and use: Prioritize a VPN with a user-friendly operating system and support for different devices, including router configurations, Windows, Chromebook, Mac, iOS, and Android. They should also have extensions for popular browsers like popular browsers like Chrome and Firefox.
- Simultaneous connections: Consider a VPN that allows multiple device connections for convenience and flexibility.
- Number of servers and their locations: More servers mean better web connection, speed, and global coverage.
- Supported VPN protocols: Choose a VPN that offers various protocols, such as OpenVPN, IKEv2/IPSec, and WireGuard, to balance security and speed.
- Logging policy: Understand the VPN’s logging policy and choose a provider with a strict no-logs policy.
- Additional features: Look for features like Kill Switch, Threat Protection, Meshnet, Double VPN, and Onion Over VPN for enhanced security and functionality.
- Customer support: Select a VPN provider with responsive customer support through multiple channels like 24/7 live chat support, email, and phone.
- Payment methods: Consider a VPN that offers a wide range of payment options, including cryptocurrencies, prepaid cards, and digital wallets, for convenience and privacy.
- Money-back guarantee: Choose a VPN with a risk-free money-back guarantee to test the service and ensure customer satisfaction.
- Multilingual app: Look for a VPN with a multilingual app to enhance accessibility and cater to a diverse user base.
Uses of a VPN in 2024
Once you’ve chosen a good VPN for your needs, you’ll be able to do all sorts of things that were previously not possible. A VPN offers a range of practical applications to enhance your online experience.
It allows you to hide from government surveillance, bypass censorship to access restricted content, freely use platforms like Kodi, unblock websites at school or work, protect your data and identity, maintain privacy by hiding your online activity, access geo-restricted services such as Netflix USA, and browse safely on public networks.
With these handy features, a VPN becomes an essential tool for a safer and more versatile internet experience. Here are some uses of a VPN in 2024
- Protect Your Identity and Personal Data: When you connect to the internet, your ISP assigns you an IP address. This IP address can be used to track your online activity and even personally identify you. A VPN encrypts your traffic and routes it through a server in another country. This gives you a new IP address, making it impossible for anyone to track your online activity or personally identify you.
- Bypass Government Censorship: Countries like China, Russia, and Iran have strict censorship laws that block access to certain websites and online services. A VPN allows you to bypass government censorship and access blocked websites and services.
- Unblock Geo-Restricted Content: Streaming platforms like Netflix, BBC iPlayer, and Hulu use geo-restrictions to control which countries can access their content. A VPN allows you to unblock geo-restricted content by spoofing your location. This gives you a local IP address, allowing you to access the content that you want. Make sure you choose the best VPN for streaming that can unlock at least 15+ catalogs of major streaming platforms.
- Install It On Your Router: If you want to protect all the devices in your home, you can install ExpressVPN on your router. This will allow you to connect all of your devices to the VPN with one account. You’ll also be able to cover devices that don’t support native VPN apps including Apple TV, Roku, Xbox, PS4, and more. Plus, if you have a VPN that has a limit on simultaneous connections, setting it up on your router will only count as one!
- Bypass ISP Throttling: ISP throttling can be frustrating as they often throttle internet speeds for certain activities like streaming video or downloading files. When you’re using a VPN, your ISP can’t see what you’re doing online. This means that they can’t throttle your internet speeds for any activity.
- Protect Your Privacy on Public Wi-Fi: Public Wi-Fi is convenient but it’s also dangerous. Cybercriminals can set up fake Wi-Fi networks to steal your personal data. A VPN encrypts your traffic and routes it through a server in another country. This makes it impossible for anyone on the public Wi-Fi network to see what you’re doing or steal your personal data.
- Online Gaming: A VPN can improve your online gaming experience by reducing lag and protecting you from DDoS attacks. It also encrypts your traffic, making it impossible for anyone to DDoS you as your real IP address is hiding behind a VPN-generated IP. Therefore, you can enjoy lag-free gaming with the best VPN for PUBG and Fortnite. So make sure you choose the best VPN for gaming so you can have a smooth experience while pulling a 1 vs. 5 clutch.
- Download Torrents Anonymously: Torrenting is often associated with piracy and copyright infringement. To avoid getting in trouble, it’s important to download torrents anonymously. When you use a VPN for torrenting, it makes it impossible for your ISP or anyone else to see that you’re downloading torrents as the VPN encrypts your traffic. This protects you from getting in trouble with copyright holders or your ISP.
- Avoid Trackers and Advertisers: Ad trackers and advertisers use cookies to track your online activity and serve your targeted ads. When a VPN encrypts your traffic, it also hides your IP address. This makes it impossible for ad trackers and advertisers to track your online activity or serve you targeted ads.
- Escape Dynamic Pricing: Dynamic pricing is a pricing strategy that charges different prices to different customers based on factors like location, time of day, and browsing history. By using a VPN to change your location, you can avoid dynamic pricing. For example, you can connect to a server in a country with cheaper flights and book your tickets at the same price as locals.
- Engage in P2P/Torrenting Activities: Probably one of the main reasons why anyone comes looking for a VPN in the first place! The technology allows you to download torrents securely and anonymously.
- Access to Geo Restricted Streams: VoDs have a different library based on region. If you are based in New Zealand or Australia, you can use a streaming VPN to unblock more movies/TV shows. All you require is the best VPN for New Zealand and Australia to get the best streaming results.
- Leverage Online Privacy/Security: VPNs mask your IP address and shift your location to different countries. This ensures all your online activities remain untraceable while protecting you from the prying eyes of hackers, copyright infringement, and surveillance agencies.
- Protection from DDoS Attacks and Swatting Hoaxes: By connecting to a local VPN, you can boost speeds to distant destinations. Subsequently, you benefit from smooth overseas gaming, while securing yourself from DDoS attacks and swatting hoaxes.
- Unblocking Social Media in Countries with Tough Laws: If you get a VPN into China, you can also bypass the “Great Firewall” and VPN bans on social media like Facebook, Twitter, or YouTube.
Methodology: How we tested these VPNs
In our testing process, we followed a rigorous methodology to evaluate the VPN reviews based on the following factors:
- Speeds: We conducted thorough speed tests to assess the performance of each VPN, measuring their download and upload speeds to ensure fast and reliable connections.
- Privacy and Security: We examined the privacy policies and security features of each VPN, analyzing their encryption methods, logging practices, and overall commitment to user privacy.
- Servers: We evaluated the number and distribution of servers offered by each VPN, ensuring a wide range of server locations for optimal performance and access to geographically restricted content.
- Prices: We considered the pricing plans and subscription options provided by each VPN, assessing their affordability and value for money in relation to the features and services offered.
- Unblocking: We tested the VPNs’ ability to bypass geo-restrictions and unblock popular streaming platforms, ensuring users can access their desired content from anywhere in the world.
- P2P Support: We examined the VPNs’ support for peer-to-peer file sharing, assessing their compatibility, speed, and level of anonymity for torrenting activities.
- Apps and Compatibility: We evaluated the availability and functionality of VPN apps across different devices and operating systems, ensuring compatibility and ease of use. Each VPN is tested on multiple platforms like Windows, Mac, Linux, Android, iOS, Firestick, Xbox One, Nvidia Shield, Kodi, and more. We specifically looked for the best VPN for Apple TV, and Roku for great streaming accessibility.
- Reliable Support: We interacted with the VPNs’ customer support teams to assess their responsiveness, knowledge, and effectiveness in addressing user queries and concerns.
- Money Back Guarantee: We considered the presence of a money-back guarantee offered by each VPN, providing users with the option to request a refund if they are not satisfied with the service.
By conducting comprehensive tests and assessments across these factors, we aimed to provide users with reliable and informed recommendations for selecting the most suitable VPN for their needs.
Are VPNs Legal and Safe to Use?
Yes, using a VPN is generally legal and safe in most countries. VPN usage is unrestricted in the US, the UK, Canada, and many European countries. However, it’s important to note that there are a few exceptions. Some countries, particularly those with strict limitations on freedom, have placed restrictions on VPN usage.
Different countries around the world may have exclusive laws, which may place restrictions on using VPN services.
For instance, those located in China, Russia, and Iran, Oman, can only use government-approved VPN services (that definitely cannot be considered safe).
In the UAE, anyone caught using a fraudulent IP address could face imprisonment or fines of up to $400,000. Other countries where VPNs are banned include Turkey, Iraq, Belarus, and North Korea!
How Do I Get a VPN?
The simplest and most convenient way to get a VPN is to configure it on your preferred device. You can easily get dedicated apps that are compatible with your devices to download a good VPN. The popular premium VPNs offer apps for all major operating systems to ensure a safe and secure connection.
To easily set up the VPN app on your device, follow the given steps:
- Download and install a reliable VPN. We recommend ExpressVPN for ultra-fast and super-secure connections.
- Launch the VPN app, register an account, and log in
- Search and connect to the available server that you like
- Enjoy secure browsing!
FAQs – Best VPN Services of 2024
💭 Which VPN is best in 2024?
⭐What is the actual best free VPN?
💭What is the best VPN for iPhone?
📍Is it worth paying for a VPN?
⭐How do I choose the right VPN for me?
💭What is a mobile VPN?
📍What's the best VPN for gaming?
⭐What's the most secure VPN for privacy?
💭What is a remote-access VPN?
📍Which is the best VPN with full speed?
💭What VPN to use for Netflix?
📍Which VPN is safest?
💭Is it bad to use a free VPN?
📍Can VPNs be hacked?
📍Can VPNs steal your data?
💭 How Much Do VPN Services Cost?
Wrapping Things Up
In conclusion, when selecting the best VPN for your needs, it is crucial to consider several key criteria. These criteria include the logging policy, potential IP leaks, speed, torrenting capabilities, Netflix unblocking, server count and locations, simultaneous connections, the presence of a kill switch, and the jurisdiction of the VPN parent company. By evaluating these factors, you can make an informed decision about which VPN to choose.
Our top picks for the best VPN services in 2024 include NordVPN, Surfshark, and ExpressVPN. NordVPN stands out as our overall top choice, offering high-speed servers, robust encryption, and a range of features suitable for both businesses and individuals. Additionally, it provides excellent value for its affordability.
Surfshark, while a newer player in the VPN market, has quickly gained recognition due to its strong encryption protocol, high-speed servers, and user-friendly app. ExpressVPN, a well-established and highly popular option, offers top-notch features, including high-speed servers, strong encryption, and a reputation for reliability, although it is one of the pricier options available.
Remember, choosing the best VPN and top VPNs involves considering your specific requirements and priorities. By carefully weighing the criteria and evaluating the top VPN services, you can find the ideal solution to protect your online privacy and security.
For more detailed insights and guidance on how to access geo-restricted content, as well as the latest trends in the streaming world, visit StreamingRant.